What is a Replay Attack and How to Prevent it?
Victims of replay attacks are robbed of data confidentiality, credentials, and, most times, huge amounts of funds.
Internet and data breach is widespread, and many companies now face advanced-level cyber threats. 'As the world goes digital, so do real-world criminals metamorphose into "digital" criminals'. The most recent form of cyber threat, known as the replay attack, poses many risks to public and private networks. Victims of replay attacks are robbed of data confidentiality, credentials, and, most times, huge amounts of funds.
While storing data online is super helpful, the lack of digital security makes it incredibly risky.
Read through this article to understand what a replay attack means, how it works and how to secure your network from replay attacks. But before anything else, let's go through what replay attack means.
What is a Replay Attack?
A replay attack, also called a repeat attack, is when an attacker pries, intercepts, and "replays" an encrypted data transmission, allowing the attacker to interact with the receiver as though they were the original sender.
The attacker does not need advanced skills to decrypt a message after capturing it from the network. Once they can copy and resend the whole data, the attack is successful. A replay attack is one of the most common and simple forms of cyber attack.
Illustration of a Replay attack
1.A relatable illustration of a replay attack is; When someone with evil intent somehow sniffs say your "backup code," inputs the code along with your username on their browser, and is able to access your account details on social media, email, or bank account profile. They can pose as you or even make away with thousands/millions of cash from your account.
2.While in the Crypto industry, a replay attack goes this way;
In a valid transaction between Jane and John, say Jane is the sender while John is the receiver. Assuming Jane wants John to transfer $150 from his account to hers, Jane sends an authentic message to John to place this request. Since John trusts(hashed password) Jane, he sends her the money immediately.
But here, the cheat comes in a replay attack.
While Jane sends her hashed password to John over the network, Alice (the attacker) eavesdrops on the transaction, copies the hash, and tries to replicate it. John sees a message; he thinks it's from Jane, so he transfers the required money. However, this time the money is transferred to the attacker(Alice) instead of Jane. The replay attack is complete.
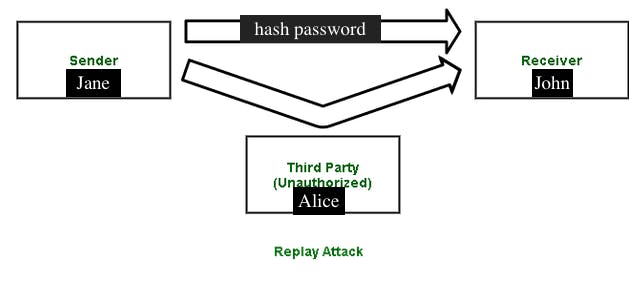 Malicious hackers go through replay attacks to steal funds and breach networks.
The attacker doesn't need to know the password; he only needs to copy the whole hash message over the network without decrypting.
Malicious hackers go through replay attacks to steal funds and breach networks.
The attacker doesn't need to know the password; he only needs to copy the whole hash message over the network without decrypting.
How Do You Prevent a Replay attack?
1. Timestamping
By creating a timestamp on the server and setting it to reject any requests older than a specified time frame, the server can identify which messages fail to meet the time-range requirements and then discard them. Timestamping is an effective approach to stop a cybercriminal from initiating a replay attack.
2. One-time password (OTP) or Random session key
One-time password or the session key becomes invalid once it has been used or after a short time if unused. Implementing the OTP or random session key strategy ensures that even if the message is copied and resent by an attacker, the encryption key shows expired and can no longer be reused.
3. Use secured networks
Data can be protected from replay attacks by ensuring internet activities are carried out only on websites that use the HTTPS protocol and avoiding public or free Wi-Fi. Also, since replay attacks require the attacker to gain access to your network, using a VPN hides your internet activity from third parties, which stops hackers from coming over.
4. Digital Signature
A digital signature is a complicated process that involves algorithms and "keys." Every computer has a unique private key that only the computer knows. The use of digital signatures makes it easy for the recipient to verify that the sender is true and who they are.
Bottom Line
Replay attacks present real danger to network security when they are successful. Since the attacker doesn't require any additional tools or abilities to carry out this attack, it appears to be an easy workaround for cybercriminals. However, securing your access points through one or more of the methods in this article can help you prevent replay attacks.
